In October, cyber criminals developed new twists on old familiar schemes to redirect users from popular web sites to bogus resources, z`and thus demonstrated that the number of Internet fraud techniques is infinite. Virus makers also exploited the popularity of some of the most notorious malicious programs to spread their malware under the guise of a vaccine that protects against them. Meanwhile, the battle between viruses and anti-viruses is gradually moving onto a new field: the x64 platform.
Anti-rootkit x64
On October 26, 2010, Doctor Web released a beta-version of its free utility Dr.Web CureIt! featuring two versions of the anti-rootkit module Dr.Web Shield which are designed to be used under the 32- and 64-bit versions of Windows. The improvedDr.Web CureIt! detects the 64-bit version of BackDoor.Tdss and can cure it.
A distinguishing feature of this malicious program is its bootkit components which allow it to load before an operating system is started, thus controlling an OS’s loading process and bypassing protection mechanisms that prevent the installation of unsigned drivers. Once the malicious driver is installed, the rootkit can covertly perform its malicious tasks in the system. When testing of the Dr.Web CureIt! beta is over, the scanner will be incorporated in all Dr.Web anti-viruses for Windows.
Ill fame for ill intentions
At the same time anti-virus companies are studying new malicious programs and making their findings available to the media, who in turn alert users to the dangers, criminals are also using this knowledge to spread their malicious programs, disguising them as tools that will neutralize other, more notorious ones.
In October, Doctor Web’s virus analysts discovered three incidents of such fake utilities being spread. The most well-known of these involved the mailing of a utility that was supposedly being offered by a renowned anti-virus vendor to neutralize the notorious Trojan.Stuxnet. Dr.Web detects the fake utility as Trojan.KillAll.94. Reports about this Trojan were received from European users.
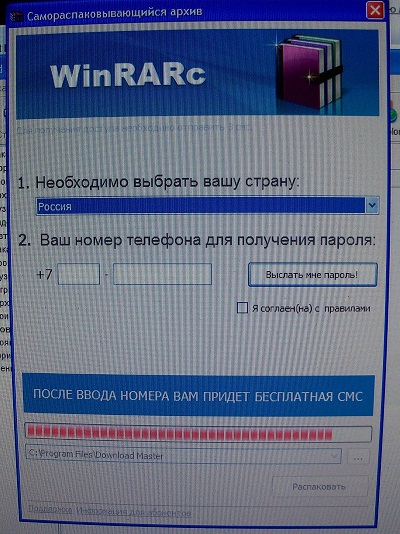
Distributors of fake self-extracting archives (Trojan.SMSSend) realized that certain types of their "products" (e.g. WinRARC) were gaining in popularity and that some users were failing to notice that such "archives" didn't contain any useful information. This encouraged criminals to go further: they began spreading other fake archives as utilities for extracting files compressed with WinRARC. No doubt, a user had to send a certain amount of money to criminals in order to use the "utility".
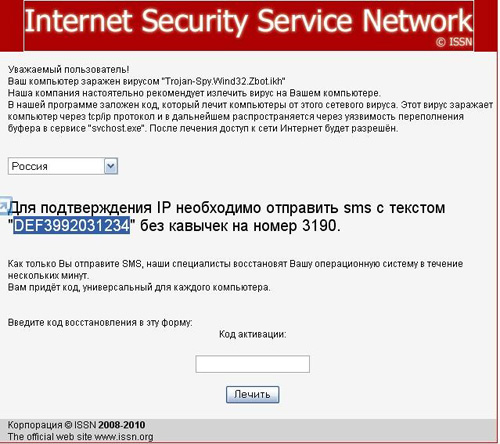
A new modification of Trojan.Hosts, appeared in the wild at the end of October. The malware targeted Russian users, informing them that their respective systems were infected by a variation of Zbot (Trojan.PWS.Panda under the Dr.Web classification), and prompted them to send a paid short message to get their systems cured.
Internet fraud in October
The number of requests for support (available free of charge to victims of cyber fraud) in October didn't differ much from that of September: 118 requests per every 24 hours vs. the September figure of 124.
Most requests were received in the first two weeks of the month when Trojan.HttpBlock. was found in large numbers in the wild. In the peak period, the number of requests related to the Trojan per day could reach several hundred (up to 80% of all requests).
This program redirects a web browser to pages received from a web server installed by Trojan.HttpBlock in the compromised system. Criminals demand a ransom from victims to regain access to web sites.
When, on October 14, Doctor Web issued a warning about the wide spreading of Trojan.HttpBlock, short code aggregators promptly blocked criminals' accounts, cutting the number of support requests related to Internet fraud to 50–70 per 24 hours.
With the number of Trojan.HttpBlock incidences diminishing, top spots for the most widely spreading malware once again went to Windows blockers (Trojan.Winlock), that demand cell phone account balance refills and Trojans that modify the hosts file to redirect users, who frequently visit social networking sites and other web resources, to bogus sites.
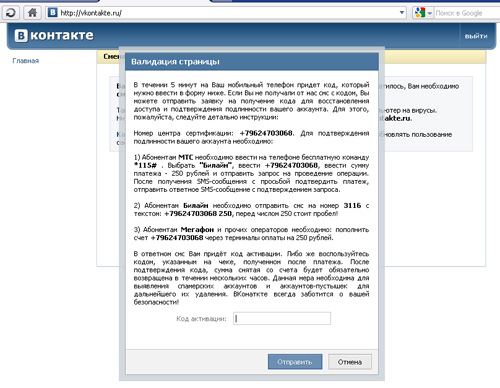
It should be noted that towards the end of October, criminals were tending to use schemes that lured victims into providing their cell phone numbers and replying to a free short message. These users subsequently wound up as subscribers to a paid service. This scheme, which has been around for a long time, has become popular again. But while previously it was used mainly on fraudulent web sites, it is now employed to spread malware like Trojan.SMSSend and Trojan.Hosts.
In addition, a slightly modified ransom scheme that involves mobile phones has been discovered. Here a user doesn't need to search for an ATM, but can pay criminals instantly by dialing a service command or by sending a special short message.
Internet swindlers kid around too
An insignificant number of Trojan.Winlock modifications discovered in October didn't demand any unlocking codes from users. On the contrary, the text displayed in the blocking window warned users about the dangers of frittering their lives away on a popular social networking site, ultimately asking them to reflect on whether they are persons or puppets.
Other events worth mentioning here include the discovery of several modifications of Android.SmsSend that covertly send paid short messages from a compromised device. Fake anti-viruses, malware featuring bootkit technologies, and Trojans targeting Internet banking users are still being found in large numbers in Europe.
Viruses detected in e-mail traffic in October
01.10.2010 00:00 - 01.11.2010 00:00
1
Trojan.DownLoad1.58681
599141 (14.92%)
2
Trojan.Packed.20878
418992 (10.43%)
3
Trojan.Oficla.zip
305686 (7.61%)
4
Trojan.Packed.20312
254743 (6.34%)
5
Trojan.DownLoad.41551
237799 (5.92%)
6
Win32.HLLM.Netsky.18401
232178 (5.78%)
7
Win32.HLLM.MyDoom.33808
179524 (4.47%)
8
Trojan.Oficla.38
120247 (2.99%)
9
Win32.HLLM.Beagle
101548 (2.53%)
10
Trojan.PWS.Panda.114
93394 (2.33%)
11
Win32.HLLM.Netsky.35328
87369 (2.18%)
12
Trojan.DownLoader1.17157
67928 (1.69%)
13
W97M.Killer
61803 (1.54%)
14
Trojan.Oficla.48
53498 (1.33%)
15
Trojan.PWS.Panda.387
51020 (1.27%)
16
Trojan.Oficla.73
45969 (1.14%)
17
Trojan.Botnetlog.zip
42480 (1.06%)
18
Trojan.AVKill.2788
35663 (0.89%)
19
Trojan.DownLoader1.23313
33962 (0.85%)
20
Trojan.MulDrop1.39520
33956 (0.85%)
Total scanned:
33,579,363,132
Infected:
4,016,939
Viruses detected on user machines in October
01.10.2010 00:00 - 01.11.2010 00:00
1
Win32.HLLP.Neshta
8277556 (25.33%)
2
Win32.HLLP.Whboy.45
6770512 (20.72%)
3
Trojan.DownLoader.42350
4116047 (12.60%)
4
ACAD.Pasdoc
1616962 (4.95%)
5
JS.Nimda
1334519 (4.08%)
6
Exploit.Cpllnk
862594 (2.64%)
7
Win32.HLLM.Dref
714726 (2.19%)
8
Win32.Virut
596437 (1.83%)
9
Trojan.Click.64310
469055 (1.44%)
10
Win32.HLLP.Rox
458892 (1.40%)
11
Win32.Antidot.1
450340 (1.38%)
12
Trojan.Click1.6029
447519 (1.37%)
13
Win32.Rmnet
400975 (1.23%)
14
Win32.HLLW.Shadow.based
282147 (0.86%)
15
Trojan.Smorchok.334
221668 (0.68%)
16
Win32.HLLP.Whboy
220591 (0.68%)
17
Win32.HLLP.Novosel
213851 (0.65%)
18
Trojan.DownLoader.46199
156212 (0.48%)
19
BackDoor.IRC.Sdbot.4590
154582 (0.47%)
20
Trojan.DownLoad.32973
136309 (0.42%)
Total scanned:
84,690,812,733
Infected:
32,677,797
View the article