June 21, 2012Russian anti-virus vendor Doctor Web is warning users about a new version of the Android.SpyEye program that intercepts incoming short messages received by mobile devices. This Trojan is disguised as Android Security Suite Premium, allegedly protecting smartphones from malicious software.The new version of the Trojan also has a shield icon and is added to the virus database as Android.SpyEye.2.origin. When the program is started on a mobile device, it also displays the shield splash screen and an activation code.

Experts already reported this Trojan several days ago, but Doctor Web's virus analysts managed to study the program in more detail. Android.SpyEye.2.origin is a spy Trojan whose main goal is to get access to SMS messages arriving at a mobile number from a banking system when certain transactions are carried out. Such messages contain an mTAN code that a user has to enter into a special form to confirm a money transfer. The Trojan monitors a number of system events: SMS_RECEIVED (receipt of a new SMS message), NEW_OUTGOING_CALL (outbound call from the mobile device) and BOOT_COMPLETED (loading of the operating system). Cybercriminals are able in some way to control the Trojan remotely. When a new message is received, Android.SpyEye.2.origin checks whether it contains a command meant for the malware. If it does, the Trojan executes it and removes the message. Attackers can instruct the Trojan to do the following:
- Enable the mode in which the Trojan forwards all new messages to a number specified in the message containing the command.
- Toggle off of this mode.
- Delete the Trojan horse.
If no control command is found in the incoming message, the message information is added into a special database.The Trojan waits for 180 seconds after the operating system has been loaded or until it detects an outgoing call and then adds information about the last incoming SMS message to the same database. If the information had been added into the database earlier, this pre-existing data is uploaded to the criminals' server.
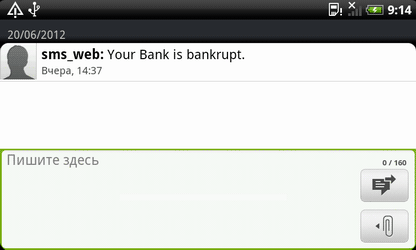
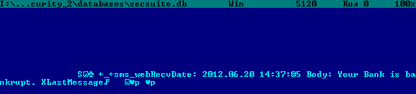
It should also be noted that after processing an incoming SMS, the Trojan sends the device's ID and phone number to a server belonging to intruders.So, in addition to banking data (mTAN-codes), criminals can also get hold of other important information such as private correspondence.Devices running Dr.Web anti-viruses for Android are protected from this malicious program: the Origins Tracing ™ technology enables Dr.Web to successfully detect all of its modifications.
View the article






