Russian anti-virus company Doctor Web is warning users about a new Trojan targeting Android devices. The malware poses a threat to devices connected to the network operated by China Mobile. Having infected a mobile device, Android.MMarketPay.origin will purchase applications in the carrier's electronic store, significantly reducing the funds in the subscriber's account.
In accordance with modern trends, China Mobile has its own Mobile Market that offers users both free and chargeable content. The Mobile Market uses a standard purchase procedure: upon purchasing an item, the buyer is given a confirmation code that they must then enter in order to complete the transaction. This is done to prevent people from making accidental purchases . The corresponding amount is debited from the subscriber's account.
The main objective of the new malware Android.MMarketPay.origin is to purchase apps in the store without user consent. The Trojan performs all the steps automatically: it intercepts verification codes and confirms purchases. This malicious program may have been designed to increase the profits of unscrupulous application developers or to discredit China Mobile and do harm to its subscribers.
Android.MMarketPay.origin is embedded by criminals into programs distributed via Chinese forums and sites distributing applications. The image below shows features available to users after installation (features provided by a legitimate application are listed on the left, while functions available with a modified version are on the right).
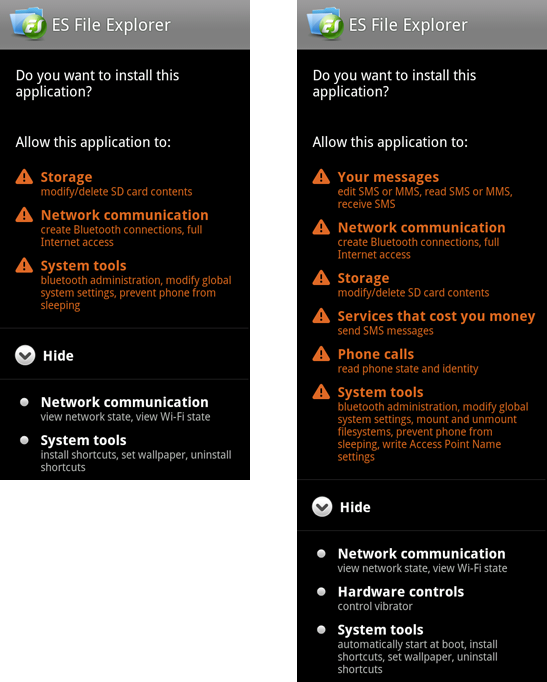
Access to SMS messaging is necessary to intercept confirmation codes. Moreover, Android.MMarketPay.origin can also bypass CAPTCHA tests: it sends images to a special server for analysis.
Doctor Web recommends that Android users be vigilant and install applications obtained only from trusted sources. Devices running Dr.Web products for Android are protected from this malicious program.
View the article






