Experts have repeatedly stated that the more popular an operating system is, the more interested virus makers are in it. This assertion can surely be applied to the operating system Android.
Android.SmsSend — little SMS Trojans family
One of the first references to this Trojan in the media was on August 4, 2010. That seems quite recent. However, it is hardly surprising. The mobile market is very dynamic, and virus writers also have to be creative and act quickly.
This was the day a user of the popular Russian forum 4pda.ru/forum, which is devoted to mobile phones, smartphones, and PDAs, added a post describing an issue related to a certain program (a video player) downloaded from the Internet. Privileges defined for this program allowed it to work with SMS, or, more precisely, to send SMS; the permission SEND_SMS was enabled. The next day another forum visitor reported a problem in connection with this file. The file's name was RU.apk. The file featured a video player icon
 with the name: MoviePlayer. Interestingly, the created date for files in the package was July 29, 2010. It turns out that the Trojan distributed undetected for nearly a week.
with the name: MoviePlayer. Interestingly, the created date for files in the package was July 29, 2010. It turns out that the Trojan distributed undetected for nearly a week.Forum users sent the suspicious file to anti-virus companies on the 5th of August. It was then that Android.SmsSend.1 was added to the Dr.Web virus database. A bit later the same malicious program was added to the virus databases of other anti-virus vendors.
On September 7, 2010, a small post from Doctor Web describing a new version of Android.SmsSend with a different icon and package name was published in the Android section of http://www.mobile-review.com.
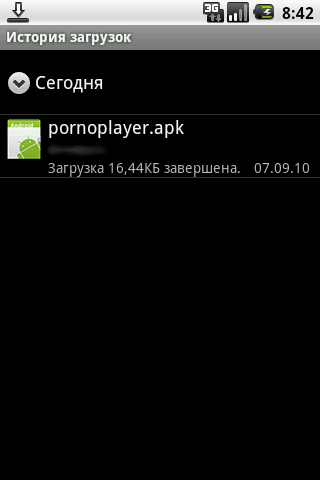
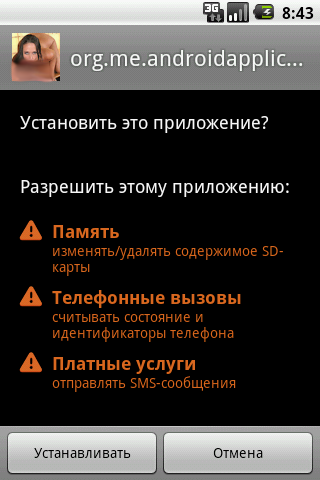
The new modification was added to the virus database on the same day, September 7, 2010, under the name Android.SmsSend.2. How and when it detects Android.SmsSend.1, detection of foreign anti-virus products will appear later, which is quite logical, given that the Trojans of the family are aimed at smartphone users in Russia.
No other news about SMS Trojan horses for Androidwas was available for about a month, except heated discussions regarding the already detected versions Their appearance caused a great deal of controversy among both professionals and users. Some people believed that it was impossible to get infected if the basic rules of security were observed—be careful, especially when visiting a suspicious site, and verify the permissions for programs upon their installation. Others objected that carelessness and curiosity were natural human qualities and that no precautions when visiting questionable resources would guarantee full protection against threats.
October 14, 2010, saw media reports about a new version of the SMS-Trojan horse. Its creators returned to the original player icon, and the name of the package distribution was the same: pornoplayer.apk. The corresponding database update for Dr.Web products was released on October 11.
The most interesting trait of the Trojan horse is the technique used to get it to victims’ smartphones. Owners of adult content sites (no information about other site categories is available yet) could add Trojan downloading features on their sites as part of their affiliate programmes. But the trick was that Android.SmsSend would only be downloaded when the site page was loaded by a mobile browser. If a page from such a site is loaded on an Android smartphone, the SMS Trojan horse for Android will be downloaded onto the device without the user's consent. The user may not notice anything except the rapidly fading system message displayed as the download is started. Later, by accident or out of curiosity, the owner of the smartphone can install the program, and the spicy name or carelessness, in turn, may lure the user into launching it. But If the site is loaded on any other device that doesn't run Android, the SMS Trojan horse written in J2ME will be downloaded. If a similar site page is opened on a conventional computer, the Trojan horse will not be downloaded, and the browser in most cases will open the desired site or a home page of one of the well-known search engines.
From China with Love
The peculiarity of this group lies mainly in its origin and distribution methods. We are talking about Android.Geinimi, Android.Spy and Android.ADRD (Dr.Web classification). The birthplace of these malicious programs is China. And they became famous in late 2010.
These Trojan horses are distributed under the guise of well-known programs, games, and live wallpaper. The software on this list includes programs popular worldwide, and those known only in China. Most of them are distributed via Chinese forums and websites devoted to mobile technology as well as through file sharing services.
The infection scheme in this case works as follows: A smartphone user downloads and installs such a program, runs it, and apparently it works just as expected—the user can play the game, there are no failures in the program, and the features correspond to the title. However, hidden from the user, the Trojan component is also launched. While you are enjoying the game or taking advantage of the state-of-the-art features of the program, the malicious service running in the background covertly collects your contact information, short messages, device's IMEI and SIM card data. All this information is sent to the server controlled by the Trojan horse's writers.
Android.Geinimi can determine the smartphone's location, download files from the Internet (e.g. other programs), retrieve and modify browser bookmarks and contact information, make calls, and send, process, and edit short messages. Even if the user closes the running program, the Trojan service will continue its work in the background.
In addition to retrieving and modifying contacts and short message information, sending SMS, and positioning, Android.Spycan also set itself to be launched automatically. Its authors are also able to control the Trojan horse remotely via SMS. Android.Spy can also be loaded when the smartphone is turned on, but its purpose is somewhat different—it collects the smartphone's ID information, specifies certain search parameters in the search engine forms, and opens links. The Trojan horse may download its updates, but installation still requires the participation of the user.
A typical feature of a program containing the Trojan horse is its additional permission requirements. For example, if the game in its original form only needs access to the Internet, an infected version will ask for higher privileges. So, if you definitely know that a particular program or game does not have the features that require access to SMS, calls, contacts, etc., cancelling the installation will be a wise decision.
By now Dr.Web recognizes 26 modifications of Android.Spy, 25 Android.Geinimi modifications, and 12 variations of Android.ADRD.
Android.Youlubg(Dr.Web classification) is a recently discovered malicious program. As usual, virus makers used a known program to which they added malicious features. The main function of Android.Youlubg is gathering personal information and contacting its controlling service. Another possible feature yet unconfirmed is sending SMS at a paid service number. Probably, the feature subscribes a victim to an unwanted service.
"Spy on the sly"
In addition to common Trojans, commercial spyware programs also pose a threat to Android smartphones. Depending on the developer, their features may include tracking the smartphone's coordinates, eavesdropping, retrieving information from incoming and outgoing SMS, calls, etc. Their expressly stated legitimate purpose is to monitor and protect children, monitor staff members, or verify a spouse's fidelity.
The best known commercial spyware programs are Flexispy, Mobile Spy and Mobistealth. Most developers of such programs offer their solutions for several mobile platforms: Symbian, Android, Blackberry, Windows Mobile, iPhone, iPad, Maemo (the device's jailbreak is a prerequisite for iPhone and iPad).
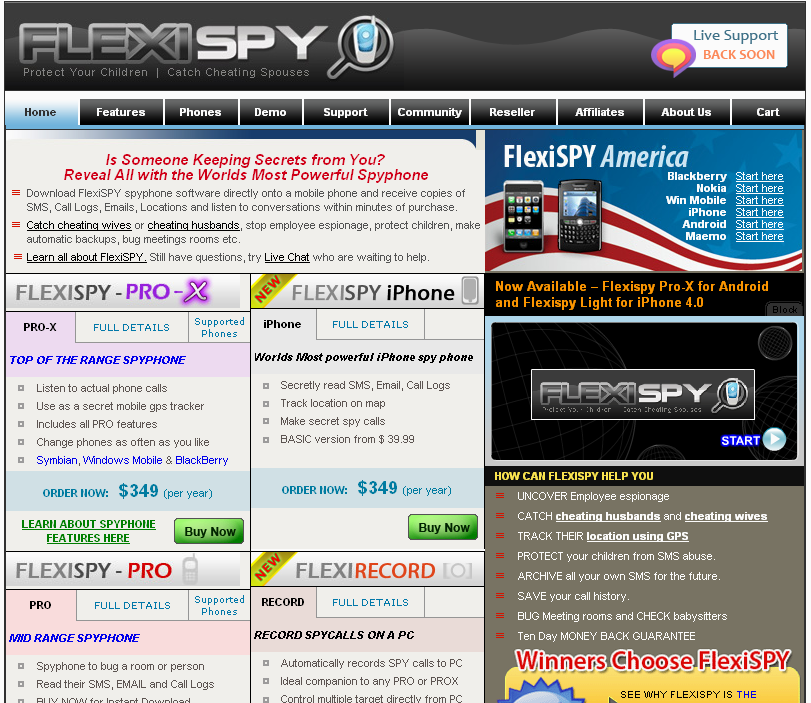
Most of the programs are available on a one-year subscription basis. The price depends on the set of features available with the particular version of the program.
To install such a "bug" on the target device belonging to the person being shadowed, physical access to the device is required since the program must be configured properly before it can be used, and all possible traces of unauthorized activity must be erased.
But how do these spies go undetected in the system?
In the case of Android, most spyware programs do not have icons on the desktop. And if they do, such icons have neutral names. If the program is launched by clicking on the icon, a special module, designed to remove all suspicion, is activated. This may be a simple game, calculator, etc. If the user checks the list of installed programs in the system menu, the spy, in most cases, will bear a neutral name or a name similar to the name of a system module.
Some commercial and free spyware programs are available in Android Market. Others can be downloaded from developers' sites directly onto the target smartphone or copied to a memory card. All these spyware programs can be used for legal and illegal purposes.
The threat from the rear
In early March 2011, the media reported that programs and games encompassing Trojan horse features were found in Android Market. Someone has added Trojan horse routines into popular software. The total number of compromised applications is almost 50.
Android.DreamExploid, the cause of this infection, can collect information about the compromised device including its IMEI, phone number, and Internet connection configuration used to contact the intruders, but most importantly, the Trojan horse installs an exploit that elevates the privileges of the smartphone's software environment. That is, instead of the standard restricted access, the user gets the permissions of a system administrator.
In addition, Android.DreamExploid can download programs from the Internet and install them without the user's consent (in cases of successful exploitation of the vulnerability).
While Google has removed all known versions of this Trojan horse from its app store and kill-switched the programs already installed on smartphones, the possibility that new versions of the Trojan horse will emerge in Android Market and on other sites can't be ruled out.
Conclusion
It has been confirmed many times that the growing popularity of an operating system inevitably increases the interest of virus makers towards that particular platform. The situation surrounding Android OS goes along with this trend.
Malicious programs are developing rapidly to keep pace with mobile device technologies. Please remember that the greater the potential of a mobile device, the more opportunities there are for malware to compromise the system and to use its features.
Undoubtedly, you need to be cautious and careful to keep your device safe. However, anti-virus software is another reliable way to reduce the infection risk. To date, Dr.Web virus databases contain entries for more than 120 malicious programs targeting Android. And, obviously, their number will grow.
View the article






