August 19, 2016
The Linux operating system remains a major target for virus makers. Doctor Web’s security researchers have examined yet another Trojan for Linux written in the Go programming language. This malware program attacks web servers that use various CMS, performs DDoS attacks, sends out spam messages, and distributes itself over networks.
The new Trojan, named Linux.Rex.1, was first spotted by Kernelmode forum users who referred to this malware as “Drupal ransomware” because it attacked websites built using Drupal. However, Doctor Web’s specialists believe that it was designed to do much more than that.
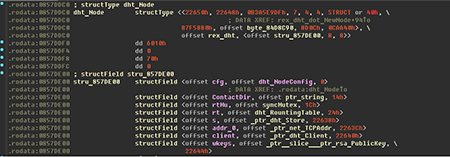
Today’s botnets can be divided into two types. Botnets of the first type use command and control (C&C) servers to receive instructions; and botnets of the second type transmit information from one infected machine directly to another and are called peer-to-peer (P2P) botnets. Linux.Rex.1 is a Trojan that can create such P2P botnets by implementing a protocol responsible for sharing data with other infected computers. Once the Trojan is launched, a computer that has been infected starts operating as one of this network’s nodes.
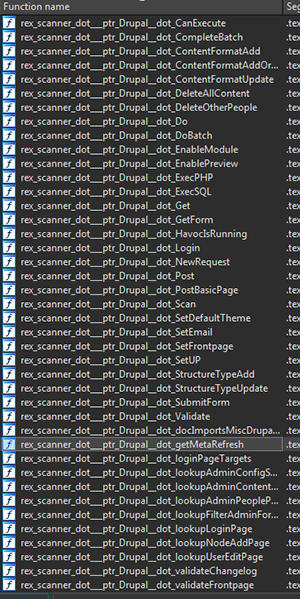
The malware program receives directives over the HTTPS protocol and sends them to other botnet nodes, if necessary. When commanded by cybercriminals, Linux.Rex.1 starts or stops a DDoS attack on a specified IP address. It uses a special module to scan the network for websites that operate using such CMSs as Drupal, Wordpress, Magento, JetSpeed, and others. It also searches for network hardware that runs AirOS, and exploits known vulnerabilities in order to get hold of user lists, private SSH keys, and login credentials stored on remote servers. However, this information cannot always be obtained successfully.
In addition, Linux.Rex.1 is also designed to be used to send out spam email messages to website owners, threatening them with DDoS attacks on their servers. If an email goes to the wrong person, cybercriminals ask that it be redirected to a website owner. To avoid being attacked, potential victims have to pay a ransom in Bitcoin cryptocurrency.
The Trojan uses a known vulnerability to hack websites built using Drupal. After performing a SQL injection, it logs itself into the system. If a site is hacked, Linux.Rex.1 loads its copy into the site and runs it. This is how the Trojan replicates itself—and is able to distribute itself without human intervention.
Linux.Rex.1 poses a serious threat to website owners and Linux users. Its signature is already in the Dr.Web for Linux database, and it is successfully detected and removed by Doctor Web Anti-virus products.
View the article