The most interesting viral events in April were related to the Android platform which drew attention of virus makers. Beside that, the last month traditionally saw discovery of several vulnerabilities in Adobe products. As before, most popular news topics became the subject of spam e-mails and were exploited in fraud-schemes at social networking web-sites. This time spammers took advantage of the UK royal nuptials.
New mobile malware
In April the first full-fledged backdoor for Android was found and now there are already two well-known modifications of the program. Android.Crusewin makes use of a few new methods to spread itself and incorporates previously unknown payload. A victim receives a message similar to the following: Updated MMS / GPRS / EDGE configuration received. Follow the link to use the new configuration: http://.../flash/MM329.apk». When the victim clicks on the link they download a Trojan APK—an Android distribution package (software is available in this format at the Android Market).
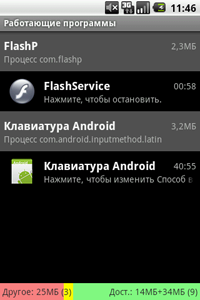

Figure 1.
After installation the Trojan downloads its XML configuration file. This malicious program is equipped with a whole set of features. For example, it is capable of sending SMS on command from the server.
In the face of growing complexity of mobile operating systems and increasing performance of devices that run them, smartphone malware also become more complex and similar in their properties to viruses for PCs. Emergence of a program like Android.Crusewind has been anticipated for quite a while. We can assume that with the spreading of anti-virus software for mobile platforms, virus writers will implement in such Trojan horses features found in other classes of malware targeting the x86 platform such as rootkits.
Several new Trojan horses for the mobile OS Android were also discovered. New versions of Android.Spy and Android.SmsSend Trojan horses were found in the wild.
Android.Spy.54 was detected on the Chinese web-site www.nduoa.com that provides access to a collection of applications for the Android platform. The Trojan horse was a part of the program Paojiao - the widget, allowing to make calls or send SMS to selected numbers. Spreading with a legitimate program is a standard method for the malware family Android.Spy to compromise smart phones.
The new modification of Android.Spy registers a background service, which connects to the malicious site and sends victim's identity information (such as the IMEI and IMSI to criminals). In addition, the Trojan horse downloads an xml configuration file containing commands that make it start sending spam SMS from the compromised device and add certain sites to the browser bookmarks.
More vulnerabilities in Adobe products
Our March review described a critical vulnerability in Adobe software. Then the traditional for such vulnerabilities term 0-day literally turned into 0-week—the vulnerability was closed in a week while several exploit samples had already been made available on the Internet.
On April 8, 2011 the public became aware of a new vulnerability CVE-2011-0611, its detailed technical description and implementation instructions followed shortly afterwards. As it happened in the last incident, here we are talking again about embedding a Trojan horse SWF-object into MS Office documents (doc-files) and PDF files. Shortly users began receiving spam messages containing exploits of the vulnerabilities Exploit.Rtf.based and Exploit.PDF.2177.
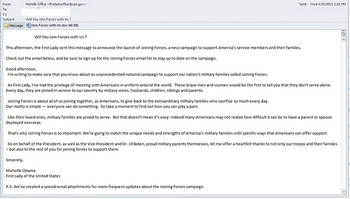
Figure 2. Exploit.Rtf.based
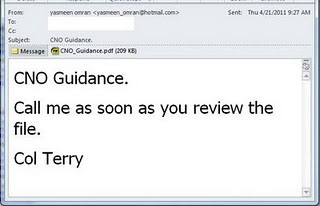
Figure 3. Exploit.PDF.2177
Mass mailings and fake anti-virus software
Also, the last month saw mass mailings containing numerous modifications of a common Trojan horse Trojan.Download.64325. Several modifications of this downloader were found in two weeks. The Trojan horse downloaded Trojan.FakeAlert.20509 to the victim's computer. Its distribution was fascilitated through the BlackEnergy botnet. Analysis of the botnet activity has revealed a significant mailing list containing a large number of corporate email addresses belonging to, in particular, pharmaceutical companies, such as SecureMedical Inc. It implies that information from e-mail addresses database may have leaked into the hands of spammers.
Fraudulent links and schemes at social networking web-sites
Fraudsters operating on social networking web-sites continue to exploit the interest of users in top news stories, while ignoring any ethical standards. Several accidents in amusement parks were recorded on video and widely publicized. Subsequently, the news about the accidents was used by criminals as a topic for Facebook messages aiming to lure users into clicking on a malicious link.
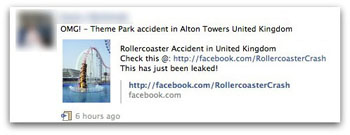
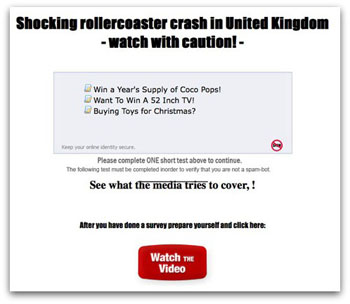
Figure 4, 5. Newsletter describing the accident in the amusement park in the UK
In other cases the news about the royal wedding served as the bait. Here the user who clicked on such links got to a site, spreading fake anti-virus software.
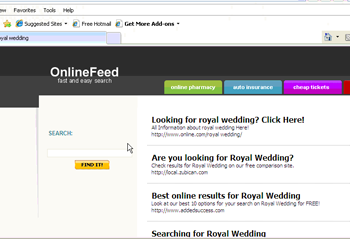
Figure 6. Fraudulent links to news stories about the royal wedding in the UK
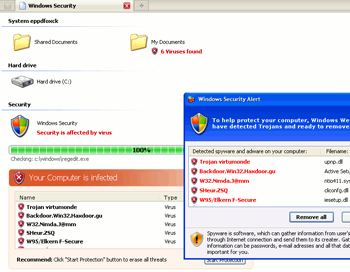
Figure 7. The fraudulent page
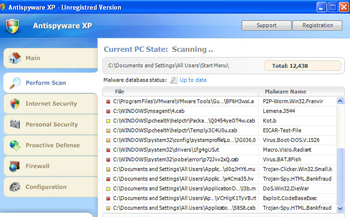
Figure 8. The interface of Trojan.FakeAlert downloaded by clicking on malicious links
Conclusion
It is certain now that a new target of virus attacks has been established. Attackers have shown a growing interest in mobile platforms. Currently techniques and experience gained by virus writers for the PC platform is being put to use to develop malware for Android which will grow in complexity and diversity. Most likely, in the near future attackers will also pay attention to the rival platform iOS.
Samples of Trojan horse software detected in April 2011 in e-mail traffic
01.04.2011 00:00 - 30.04.2011 23:00
1
Trojan.Tenagour.3
12454766 (27.22%)
2
Trojan.Inject.28090
4602849 (10.06%)
3
Trojan.Inject.27975
3548126 (7.75%)
4
Trojan.DownLoader2.22364
2805880 (6.13%)
5
Trojan.Inject.28053
2252602 (4.92%)
6
Trojan.DownLoad2.20306
1482644 (3.24%)
7
Trojan.DownLoader2.265
1111063 (2.43%)
8
Trojan.DownLoader2.17823
1098522 (2.40%)
9
Trojan.DownLoader2.1901
912229 (1.99%)
10
Trojan.DownLoader2.2035
797515 (1.74%)
11
Trojan.DownLoader2.2977
752502 (1.64%)
12
Trojan.DownLoader2.25029
653112 (1.43%)
13
Win32.HLLM.MyDoom.33808
629032 (1.37%)
14
Trojan.DownLoader2.10188
573559 (1.25%)
15
Trojan.DownLoader2.32597
563802 (1.23%)
16
Trojan.Fakealert.20459
552961 (1.21%)
17
Trojan.Inject.27968
536032 (1.17%)
18
Trojan.DownLoader2.16572
532366 (1.16%)
19
Trojan.DownLoad2.22234
526171 (1.15%)
20
Trojan.DownLoader2.30543
505686 (1.11%)
Total scanned:
32,697,947,759
Infected:
45,761,288 (0.14%)
Samples of Trojan horse software detected in April 2011 on users' computers.
01.04.2011 00:00 - 30.04.2011 23:00
1
Win32.Siggen.8
18929309 (25.86%)
2
JS.IFrame.95
18457256 (25.22%)
3
Win32.HLLP.Neshta
10341001 (14.13%)
4
Win32.HLLP.Novosel
7473876 (10.21%)
5
Win32.HLLP.Whboy.45
2744737 (3.75%)
6
Win32.HLLP.Whboy.101
2583200 (3.53%)
7
Trojan.Click.64310
1786547 (2.44%)
8
ACAD.Pasdoc
948927 (1.30%)
9
Win32.HLLP.Liagand.1
897812 (1.23%)
10
Trojan.MulDrop1.48542
685507 (0.94%)
11
Win32.HLLP.Whboy.105
580001 (0.79%)
12
HTTP.Content.Malformed
533596 (0.73%)
13
BackDoor.Ddoser.131
513468 (0.70%)
14
Win32.HLLP.Rox
423250 (0.58%)
15
Win32.HLLW.Shadow.based
213901 (0.29%)
16
Win32.HLLW.Autoruner.5555
161020 (0.22%)
17
Program.RemoteAdmin
155310 (0.21%)
18
Trojan.DownLoader2.35872
151285 (0.21%)
19
Exploit.Cpllnk
147664 (0.20%)
20
Trojan.DownLoader2.42597
143945 (0.20%)
Total scanned:
218,706,105,678
Infected:
73,187,388 (0.03%)
View the article






