July 4, 2011
The first summer month in 2011 turned out to be rich in new threats to information security. Doctor Web virus analysts found more than 40 malicious programs for the operating system Android (and only one for iOS), which indicates a steady increase in the platform's popularity among virus writers. Compared with the beginning of 2011, there has been a tenfold increase in threats to Android. Virus writers focused both on personal computers running Microsoft Windows and "Macs" didn't rest either.
Google Android under threat
Despite the fact that Android features a Linux kernel and has a reliable security mechanism, the number of malicious programs targeting this platform increases daily. One of the obvious reasons for this is the OS's very wide popularity.
Mobile devices have become a tasty morsel for the developers of malicious programs because they can be used by criminals to secretly send SMS, make calls to premium-rate phone numbers, organize promotional mailing lists based on the subscriber's address book contact information, and download content to the device. In other words, this market offers a fast track to wealth.
The fact that Android is an open-source operating system is another possible reason for the increase in threats to Android since information about a discovered vulnerability quickly becomes available to the general public. Users of Android-based devices can also download applications from different sites, which greatly increases the risk of getting infected. Yet iPhone and iPad users get content only from the App Store.
Android.Plankton, added to the virus database on June 9, became the most widely known of all malware for Android that emerged in June. This threat was identified for the first time by North Carolina State University's department of computer science whose faculty member—Associate Professor Xuxian Jiang—kindly provided Doctor Web with samples of an infected application for which the company expresses its sincere gratitude.
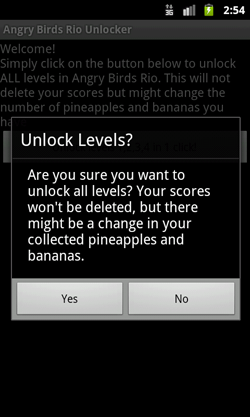
One of the distinguishing features of the Trojan horse is its probable wide distribution. The malware is built into the Angry Birds Rio Unlock application, which gives access to hidden levels of this popular game. From the Android Market alone, the infected program was downloaded more than 150,000 times, and on alternative resources such as the famous collection of applications for Android (androidzoom.com), the number of downloads reached 250,000.
The Trojan horse collects and sends criminals information about the targeted device (including its hardware ID, the SDK version, and information about the privileges of the file) but also allows intruders to execute various commands remotely.
Just a few days earlier, on June 6, 2011, Doctor Web's virus analysts found yet another threat to Android, subsequently named Android.Gongfu (currently the Dr.Web virus database contains entries for five of its modifications). The analysis revealed that Android.Gongfu exploited the same vulnerabilities as the widespread Android.DreamExploid but operated quite differently. Once launched, it elevates its permissions to those of the root account and downloads into the compromised system another application added in as a background service. When OS loading is completed, the service will start automatically without user intervention and will collect information about the affected device, including the operating system version, phone model, mobile operator name, IMEI, and the user's phone number. The collected information is transmitted to the criminals via a remote server. In fact, the Trojan horse works as a backdoor and can execute commands received from a remote server.
On June 17, 2011, signatures of four new versions of SMS senders Android.Wukong (4-7) were added to the Dr.Web virus databases. These malicious programs steal money from accounts of users running Android by sending paid short messages. The malware gets to a mobile device with an infected application downloaded by the user (they are distributed from several Chinese websites (including one of the largest collections of software www.nduoa.com) onto the device and runs as a background process. Then the Trojan horse receives a paid service number from a remote server and starts sending short messages starting with the string "YZHC" to this number at 50-minute intervals. In addition, the malicious program attempts to hide traces of its activity and removes messages it has sent as well as payment confirmations received from the device's memory.
The analysis by Doctor Web's virus analysts shows that the majority of malicious programs for Android are embedded in legitimate applications distributed through popular sites—collections of software and games. To implement attacks, criminals take advantage of operating system vulnerabilities and the carelessness of users who set high-level privileges for the installed applications.
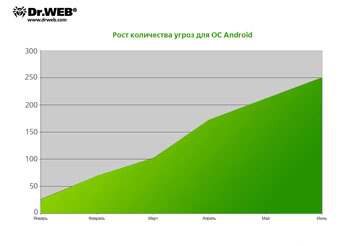
The graph below illustrates the increase in the number of threats to Android since the beginning of 2011 according to statistics gathered by Doctor Web's virus laboratory. There is almost a tenfold increase in six months, and we can assume that the number of malicious programs for this platform will rise.
We recommend that, above all, owners of Android devices pay attention to the requirements of the applications that they are going to install. For example, when installing a single-user game, it is unlikely that it really needs full access to messaging features and the address book. Surely, it is also highly advisable to protect your device with Dr.Web for Android Anti-virus & Anti-spam or Dr.Web for Android Light, whose databases contain signatures for all known threats.
MBR modification — the season's trend
Now let's have a look at the threats to the desktop. The most "fashionable" trend of June was the emergence of a large number of malicious programs that modify the Master Boot Record to compromise the system.
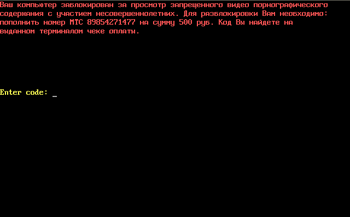
Trojan.MBRlock is the most typical example of this malware "tribe". It is an extortionist that changes the Master Boot Record making it impossible to run Windows. To date, the virus databases contain entries for about 40 versions of this Trojan horse.
Once launched, Trojan.MBRlock alters the Master Boot Record; however, the original boot entry and partition tables usually remain intact. After that, whenever a user switches on the computer, the Trojan horse blocks the operating system from loading, loads its main code from the neighbouring sectors of the hard disk into the memory, and displays a demand to refill a cell phone account (set up by the criminal). It should be noted that similarly to other Windows lockers, Trojan.MBRlock typically stops blocking access to Windows several days after it has manifested itself in the system.
However, another malicious program, Win32.Rmnet, which also modifies the MBR (so that it gets the opportunity to start before the installed anti-virus), is much more dangerous to users. It steals passwords from popular ftp-clients such as Ghisler, WS FTP, CuteFTP, FlashFXP, FileZilla, Bullet Proof FTP. This information can later be exploited to carry out network attacks or to place various malicious objects on remote servers. With this information, virus writers will be able to, at the very least, access data stored in user folders and files, and delete or modify them. In addition, malicious modules of Trojan.Rmnet can monitor network traffic and function as a backdoor.
Trojan.Rmnet gets onto computers through infected flash drives or upon launching infected executable files. In other words, it spreads like an ordinary virus since it has the ability to self-replicate—copy itself without any user intervention. The Trojan horse infects exe,. dll,. scr,. html,. htm, and in some cases doc and xls files, and can create autorun.inf files on removable storage devices. Immediately after its launch the Trojan horse modifies the Master Boot Record, registers Microsoft Windows Service (it can work as a rootkit in the system), attempts to remove RapportMgmtService, and adds several malicious modules into the system that appear in the Windows Task Manager as four entries named iexplore.exe.
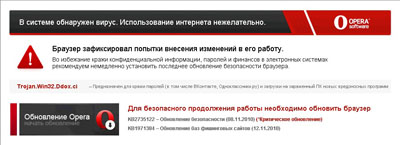
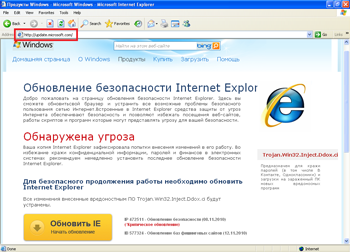
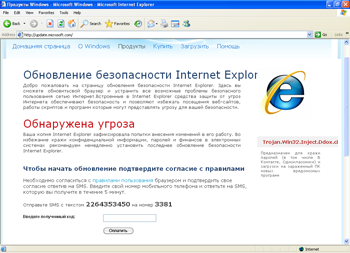
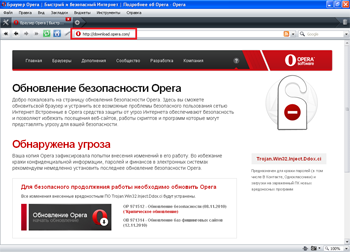
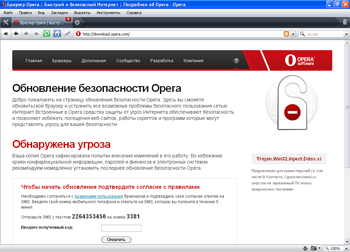
In late June, Doctor Web's technical support service received an increased number of requests related to the new malicious program Trojan.Mayachok.2. Symptoms of this Trojan infection are very easy to recognize. No matter what browser is installed on a computer (Internet Explorer, Firefox, Opera, or Google Chrome), whenever one tries to connect to the Internet, it displays a banner showing a false message warning the user that the computer has been infected by Trojan.Win32.Ddox. ci and prompting them to update the browser.
The browser address bar contains a real URL to the requested site, while the browser window shows a web page modified by the Trojan horse. If the user agrees to install the updates, he or she will be prompted to send a paid short message to the specified number.
Analysis of the threat made it clear that Trojan.Mayachok.2 doesn't modify the Master Boot Record, or the boot sector, neither does it alter ntldr, but a section of the Volume Boot Record (VBR) whose code is invoked after the MBR code. This Trojan horse uses a peculiar infection technique, quite uncommon among malware. Once in the system, Trojan.Mayachok.2 uses the system volume's serial number to create a path in the registry to detect the state of an infected system. First the Trojan horse attempts to elevate its permissions. In order to achieve its goal under Windows Vista and Windows 7, it simply restarts itself repeatedly and requests higher privileges. After that Trojan.Mayachok.2 places its loader (different versions are available for 32- and 64-bit versions of Windows) and compromises VBR but does so only if the active partition's file system is NTFS. The malware is automatically loaded into the memory while Windows is starting.
Because the malicious object is in the memory, reinstalling the browser, restoring the system, and even running Windows in the Safe Mode do not produce the desired effect.
The aforementioned leads to the following conclusion: virus writers are now more likely to implement features to modify the Master Boot Record in malicious programs, which on one hand complicates the fight against such threats, but on the other hand makes it more interesting.
"Back door" in Mac OS X
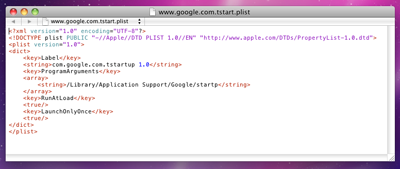
Fake anti-viruses constitute the vast majority of all threats to the Mac OS X operating system (and they are still few). The best known examples are the notorious MacDefender and various Trojan horse programs such as Mac.DnsChange. More surprising was the news of a new backdoor for Intel-compatible computers manufactured by Apple. This malware was named BackDoor.Olyx.
BackDoor.Olyx became the second known backdoor for Mac OS X—the first one was BackDoor.DarkHole. Versions of this malware exist for Mac OS X and for Windows. When launched, it enables hackers to open web pages in the default browser on the infected machine, restart the computer remotely, and perform various operations with files. The Dr.Web virus database now contains entries for BackDoor.DarkHole and BackDoor.Olyx.
This backdoor allows an attacker to control a computer without the knowledge of its owner. It receives commands to create, move, and rename files from a remote server and other instructions executed in the /bin/bash shell.
Given that, in June, Doctor Web's virus analysts added definitions for only five threats to Mac OS X and four of them were modifications of Trojan.Fakealert, the emergence of a new backdoor for this operating system is a unique event. Virus analysts from Doctor Web believe that new versions of this malware may appear in the future and will closely monitor further developments.
Malicious files detected in mail traffic in June
01.06.2011 00:00 - 01.07.2011 00:00 1Trojan.DownLoad2.2475836294 (19.08%)2Trojan.Tenagour.324929 (13.11%)3Win32.HLLM.MyDoom.5446422515 (11.84%)4Win32.HLLM.MyDoom.3380816039 (8.43%)5Win32.HLLM.Netsky.1840111150 (5.86%)6Trojan.DownLoader3.311027211 (3.79%)7Win32.HLLM.Netsky.353286816 (3.58%)8Win32.HLLM.MyDoom.based6392 (3.36%)9Win32.HLLM.Netsky5619 (2.95%)10Trojan.MulDrop1.541603068 (1.61%)11Trojan.DownLoader3.294802793 (1.47%)12Trojan.PWS.Mailer.562564 (1.35%)13Trojan.DownLoader3.449082351 (1.24%)14Win32.HLLM.Beagle2005 (1.05%)15Trojan.DownLoader3.432031903 (1.00%)16Exploit.IframeBO1849 (0.97%)17Trojan.AVKill.30971781 (0.94%)18Win32.HLLM.Perf1489 (0.78%)19Win32.HLLM.MyDoom.331425 (0.75%)20BackDoor.IRC.Sdbot.45901418 (0.75%)
Total scanned: 255,974,070
Infected: 190,176 (0.07%)
Malicious files detected on user machines in June
01.06.2011 00:00 - 01.07.2011 00:00 1JS.Click.21846639334 (39.52%)2JS.IFrame.9518224496 (15.44%)3Win32.Siggen.817706886 (15.00%)4JS.IFrame.1125804669 (4.92%)5Win32.HLLP.Neshta5706298 (4.84%)6Win32.HLLP.Whboy.455383148 (4.56%)7JS.Click.2222962341 (2.51%)8Win32.HLLP.Whboy.1011953533 (1.66%)9HLLP.Nazi.50451892928 (1.60%)10Trojan.MulDrop1.48542996382 (0.84%)11JS.IFrame.117969302 (0.82%)12Exploit.Cpllnk713024 (0.60%)13Win32.HLLW.Whboy670178 (0.57%)14Win32.Antidot.1643526 (0.55%)15Win32.HLLW.Gavir.54615365 (0.52%)16HTTP.Content.Malformed515239 (0.44%)17Trojan.DownLoader.42350422923 (0.36%)18VBS.Starter.20411382 (0.35%)19Trojan.Click.64310370556 (0.31%)20Win32.HLLP.Rox284171 (0.24%)
Total scanned: 283,468,709,281,080
Infected: 118,012,200 (0.00%)
View the article

June virus activity review: number of threats for Android increased tenfold since January
Автор
News Robot
, июл 04 2011 03:00
Нет ответов в данной теме
Читают тему: 0
0 пользователей, 0 гостей, 0 скрытых